
Introduction
Subdomain Takeover is a serious security vulnerability that allows attackers to gain control over an inactive subdomain of a website. This happens when a subdomain points to an external service (such as GitHub Pages, AWS, Heroku, or Cloudflare) that is no longer in use, but the DNS record still exists.
Hackers can claim the abandoned subdomain and use it for phishing attacks, spreading malware, redirecting users to harmful websites, or defacing web pages.
This blog will explain:
- What is Subdomain Takeover?
- How does it work?
- Real-life attack examples
- Steps to prevent it
Let’s dive in! 🚀
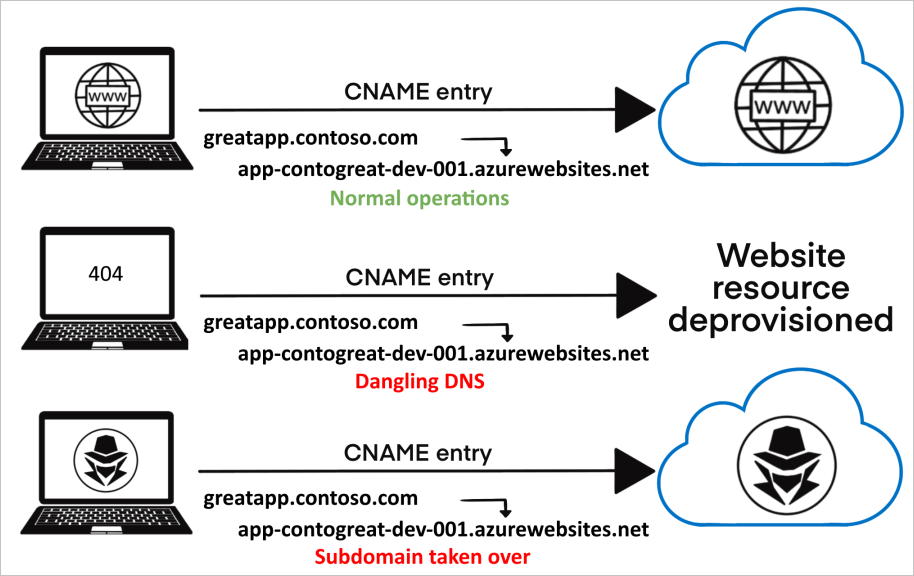
What is Subdomain Takeover?
A subdomain takeover happens when a subdomain (like blog.example.com) is linked to an external service that is no longer controlled by the original owner.
Imagine a website using Heroku to host a service at app.company.com. Later, the service is discontinued, but the DNS record is not deleted. This leaves an open door for attackers.
Steps in a Subdomain Takeover Attack:

- Finding an orphaned subdomain
- Attackers scan domains for subdomains pointing to inactive services.
- Claiming the missing service
- If a service is no longer owned, a hacker can register the same name.
- Exploiting the subdomain
- Once claimed, the attacker can host harmful content on it.
Example Scenario:
- A company uses GitHub Pages for
blog.company.com, but later removes the GitHub repository. - The subdomain
blog.company.comstill points tocompany.github.io. - A hacker creates a new GitHub Page under the same name.
- Now, they can control
blog.company.comand host phishing pages.
Why is Subdomain Takeover Dangerous? ⚠️
Subdomain Takeover can be used for many cybercrimes, such as:
1. Phishing Attacks 🎣
Hackers can host fake login pages on the subdomain and trick users into entering their passwords and personal data.
2. Spreading Malware 🦠
Attackers can upload malicious scripts to the compromised subdomain, infecting users who visit it.
3. Website Defacement 🎨
An attacker can modify the content of the subdomain, displaying offensive messages or harmful images.
4. Session Hijacking 🔓
If a user is logged in to a website, an attacker can hijack their session cookies, gaining unauthorized access.
5. Reputation Damage 💀
A hacked subdomain can harm the credibility of a business, leading to loss of trust and customers.
How to Prevent Subdomain Takeover? 🛡️
To protect your website, follow these best practices:
✅ 1. Regularly Audit DNS Records
- Check your DNS settings and remove unused subdomains.
- Use tools like Subfinder, Amass, or SecurityTrails to scan for weak subdomains.
✅ 2. Remove Unused External Services
- If you stop using a cloud service like AWS, GitHub Pages, or Heroku, delete the DNS record immediately.
✅ 3. Enable CNAME Verification
- Some platforms offer CNAME verification, ensuring that only the domain owner can use the service.
✅ 4. Set Up Subdomain Monitoring
- Use services like Detectify to track changes in subdomain activity.
✅ 5. Implement Security Headers
- Use HTTP Strict Transport Security (HSTS) to prevent HTTPS hijacking.
Conclusion 🎯
Subdomain Takeover is a dangerous cyber attack that can lead to phishing scams, malware distribution, and website defacement. Organizations should:
- Regularly check their DNS records 🔍
- Remove unused subdomains 🗑️
- Monitor for unexpected changes 🚨
By following these security measures, you can protect your website from cybercriminals. Stay vigilant and keep your digital assets secure. 🔒
Hashtags 🔖
#CyberSecurity #SubdomainTakeover #WebSecurity #DNSAttack #EthicalHacking #BugBounty #Hacker #PenTesting #CyberHelper
Backlink for More Learning 📚
For a detailed guide on securing DNS records, visit OWASP DNS Security Best Practices.
🔹 Stay Safe. Stay Secure. Protect Your Digital Assets! 🔹







