Section 67 of the IT Act: Publishing Obscene Content Online – What You Need to Know
In today’s digital world, where content spreads faster than wildfire, the line between free expression and legally punishable content can be thin. One such law that every internet user in…
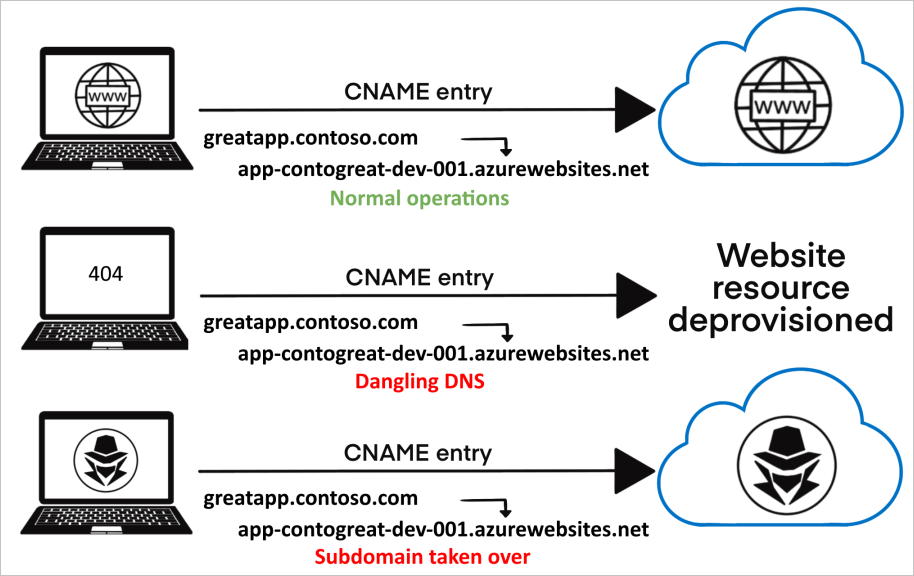
Subdomain Takeover: Understanding the Risk & How to Prevent It
Introduction Subdomain Takeover is a serious security vulnerability that allows attackers to gain control over an inactive subdomain of a website. This happens when a subdomain points to an external…
Understanding HTML Injection: A Complete Guide
Introduction The internet is filled with different types of cyber threats, and one such web-based attack is HTML Injection. It is a vulnerability that allows an attacker to inject malicious…
Understanding Cross-Site Scripting (XSS): A Deep Dive
Introduction Cross-Site Scripting (XSS) is one of the most common vulnerabilities found on websites. It allows attackers to inject malicious scripts into web pages, which are then executed in users’…
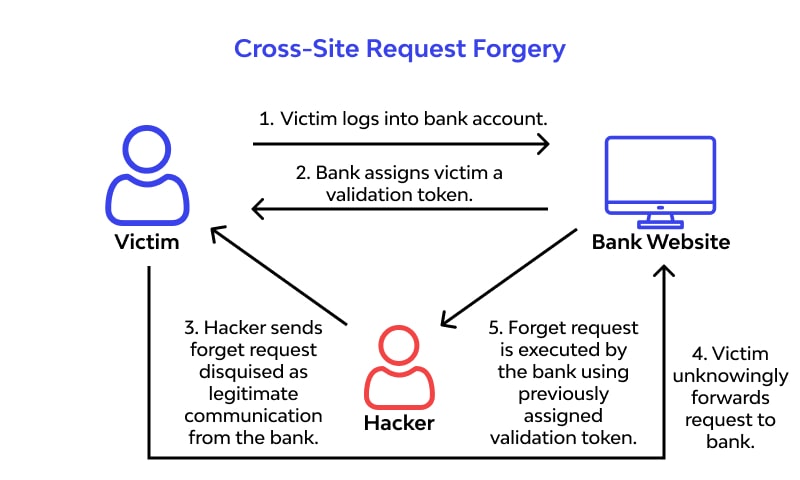
Understanding Cross-Site Request Forgery (CSRF): A Deep Dive
Introduction Cross-Site Request Forgery (CSRF) is a critical web vulnerability that forces users to execute unwanted actions on a trusted website where they are authenticated. Attackers exploit this by tricking…
Understanding OTP Bombing: How It Works and How to Stay Safe
Introduction OTP (One-Time Password) bombing is a form of cyber attack where a target receives an overwhelming number of OTP messages in a short period. This attack is used for…