Section 419 IPC: Cheating by Personation – Explained with Examples, Phishing Cases & How to Stay Safe
In an age where phishing emails, fake identities on social media, and fraudulent job offers are everywhere, knowing the law that tackles such cyber trickery is crucial. One such powerful…
Section 67 of the IT Act: Publishing Obscene Content Online – What You Need to Know
In today’s digital world, where content spreads faster than wildfire, the line between free expression and legally punishable content can be thin. One such law that every internet user in…
How to Install Kali Linux on Windows PC or Laptop Using WSL
Running Kali Linux on a Windows system has become easier and smoother, thanks to WSL (Windows Subsystem for Linux). Whether you’re a cybersecurity enthusiast or a professional ethical hacker, this…
In-Depth Guide to Cyber Law Section 66 of IT Act, 2000
📄 About This Article This article is a comprehensive guide to Section 66 of the Information Technology Act, 2000, which deals with hacking and computer-related offenses in India. The blog…
Most Common and Popular Cyber Laws in India: What Every Internet User Must Know
In today’s digital-first India, the internet isn’t just a place to browse—it’s where we shop, study, work, bank, and build businesses. But with rising internet use, comes the darker side:…
10 Best Extensions for Bug Bounty (Web Pentesting)
1. Wappalyzer What it does: Identifies technologies used on websites (CMS, frameworks, JS libraries, etc.).🔗 Download Wappalyzer 2. HackBar What it does: Helps in testing SQL Injection, XSS, and other…
Understanding CVE (Common Vulnerabilities and Exposures) in Cybersecurity
Introduction In the world of cybersecurity, CVE (Common Vulnerabilities and Exposures) plays a crucial role in identifying and cataloging security threats. It is a publicly available database that helps organizations,…
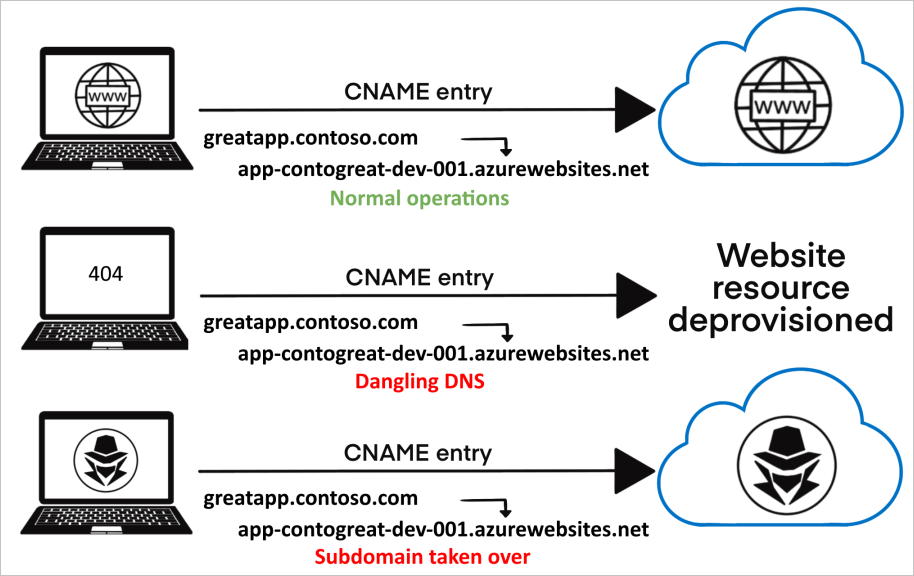
Subdomain Takeover: Understanding the Risk & How to Prevent It
Introduction Subdomain Takeover is a serious security vulnerability that allows attackers to gain control over an inactive subdomain of a website. This happens when a subdomain points to an external…
Understanding HTML Injection: A Complete Guide
Introduction The internet is filled with different types of cyber threats, and one such web-based attack is HTML Injection. It is a vulnerability that allows an attacker to inject malicious…
Understanding Cross-Site Scripting (XSS): A Deep Dive
Introduction Cross-Site Scripting (XSS) is one of the most common vulnerabilities found on websites. It allows attackers to inject malicious scripts into web pages, which are then executed in users’…